5 ways that video games have most heinously lied to us about hackers and hacking
The PSN was not hacked with a game of Pipemania. Fact
Because if you believe games, hacking is way more silly, way easier, and way more utterly insane than it is in real life. Evidence? Is it evidence you want? Good. Well I will provide you with some.
1.Hacking is always a game
Hacking, boiled down to the simplest terms, is a case of navigating through a set of security constructs to get to some nice juicy data. That involves a) problem solving, and b) an adversary of sorts. Both are, in a very loose sense at least, core elements of the video game experience itself, so why not go the whole hog, run them both through the metaphor machine, and turn video game hacking into a game within a game? Not only does this keep the flow of gameplay going, where 'real' hacking would instantly halt it with a blockade of command prompts, but if hacking in a gameis an optional pursuit, it actually encourages the player to get involved by making the mechanics a nice little mix-up from the main gameplay.

Above: We put games in your hacks in your games so you can play while you're hacking while you're playing
Also, it promotes the usage of the "Yo, dawg..." meme again. Which is basically fine.
2. Hacking looks amazing

Those command prompts I mentioned above? Forget them. Ever since Tron, that is not how computers work. Oh yeah, you may think that properly exploring all their secrets and mapping their hidden geography requires a decentunderstanding of computer science and a whole load of programming knowledge, but real computers are absolutely nowhere near as dry as some people would have you believe. All that complicatedtechnical stuff is just a smoke-screen created by those hedonistic, psychedelic experi-nauts in the programming community,in orderto keep you out of their bass-throbbing, neon-drenched world of mescalicious digital excess.
Hack a system and you will invariably find yourself whirling through some manner of day-glow cyberspace vortex made out of melted flourescent tubes and the left-over fragments of Timothy Leary's cheese dreams. A computer isn't a tool you use to access information. It's a living digi-cloud of blissed-outsynaesthetic mind-joy. And even more excitingly, if your hack fails, you'll either be trapped there forever or you'll die. Which is a bitmore glamourous thanposting abusive raps on YouTube before eventually settling out of court.
3. The password is always obvious
If you're having trouble with your hack, don't worry. Just look around your immediate surroundings. Ifyou see something writtenbackwards on a wall, directly opposite a mirror, that's your password. If not, just scroll through the security cameras (which will be easy to hack)until you find a room with a giant whiteboard in it. It'll probably have "PASSWORD01" written on it in big letters. That's how you'll know it's the right one.
Sign up to the GamesRadar+ Newsletter
Weekly digests, tales from the communities you love, and more
4. If the password is not obvious, the password prompt will help you
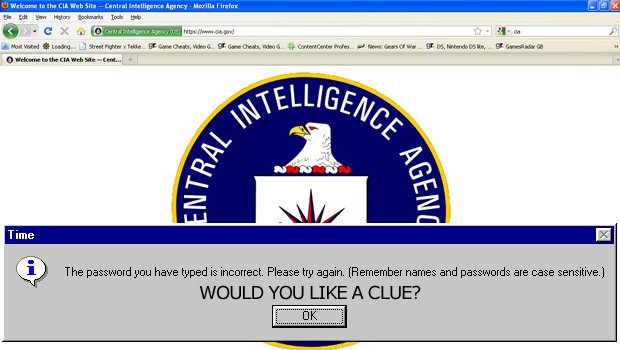
Yeah. As video games have taught us, all computer systems want to be hacked. It's pretty boring for them, just sitting around all day being massive and full of knowledge, and they crave a bit of human interaction. Those mainframes just loveindulging in a bout ofplayful "Riddle me this" action, so as soon as they spot a hacker trying to break in, they'll immediately make friends and start up a little game. Screw those tech security guys and their precious data. They haven't called in months. A video game computer won't give you a blunt "Password incorrect" message before alerting security. It'll tell you which letters you have right and give you a couple more tries to get the rest.
5. Any piece of hardware can be hacked
Everything is networked. Fact. If it uses an electrical current, steam-power, or just plain old has moving parts, then it is run online as part of onehuge, universalnetworkand can be hacked. Security door, drone turret, fruit machine or novelty cigarette lighter. It doesn't matter what it is. If it is a device and you are a hacker, then you can take control of anything from anywhere and have it do your bidding. No local connection is needed, no specialist hardware is needed. Just log onto GenericNet (tm) using the laptop, smart phone orTiger LCD game of yourchoice, and it is yours.

In the real world, this does not work.
June 20, 2011



